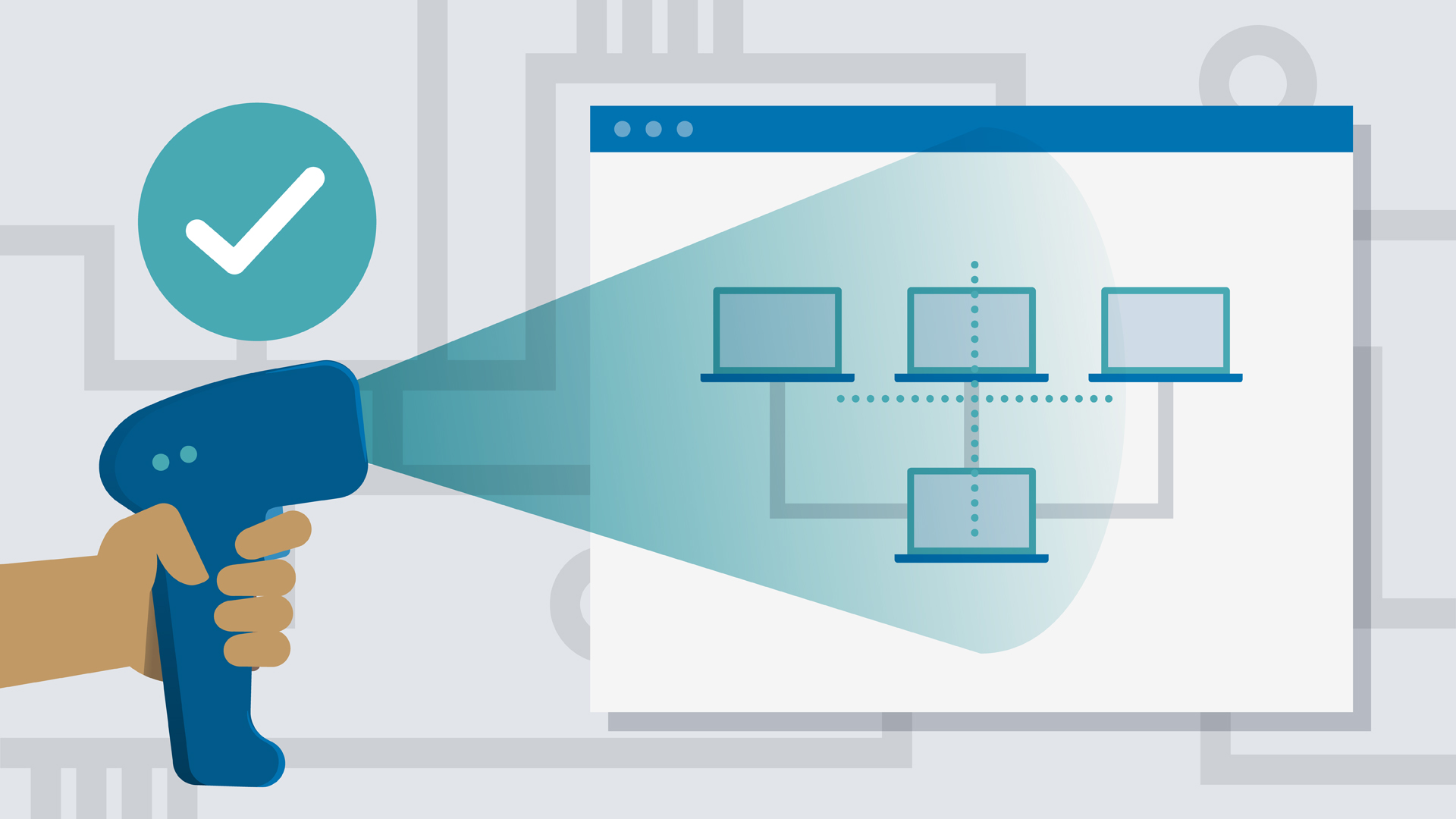
The MITRE ATT&CK Framework is becoming an excellent source to understand the adversary tactics and techniques. The framework provides native Windows tools and commands that are used by an adversary to perform man action to include “Remote System Discovery” T1018.

Mitre:
Examples of tools and commands that acquire this information include “ping” or “net view” using net. The contents of the C:\Windows\System32\Drivers\etc\hosts file can be viewed to gain insight into the existing hostname to IP mappings on the system.
2 Primary Tools used for Remote System Discovery:
- ping
- net
There is another method not very known to most folks but has been used by adversaries when ping & net are unavailable to them.
tracert (TraceRoute)
The TRACERT diagnostic utility determines the route to a destination by sending Internet Control Message Protocol (ICMP) echo packets to the destination. In these packets, TRACERT uses varying IP Time-To-Live (TTL) values. (From Microsoft)
Slow but effective!
C:\Users\admin>ping 192.168.1.1
Access is denied.
C:\Users\admin>net view
Access is denied.
C:\Users\admin>tracert 192.168.1.1
Tracing route to 192.168.1.1 over a maximum of 30 hops
1 <1 ms <1 ms <1 ms 192.168.244.2 2 1 ms <1 ms <1 ms 192.168.1.1 Trace complete.
C:\Users\admin>
The example above is of a system that has prohibited ping & net command, but an adversary can use the tracert command to find live hosts and help map out the network.